Security
SunFlare's services are based on a proprietary system designed to deliver documentation securely and reliably. We aim to provide optimal solutions based on the principles of quality and security, both of which are essential requirements in business.
Our robust security system
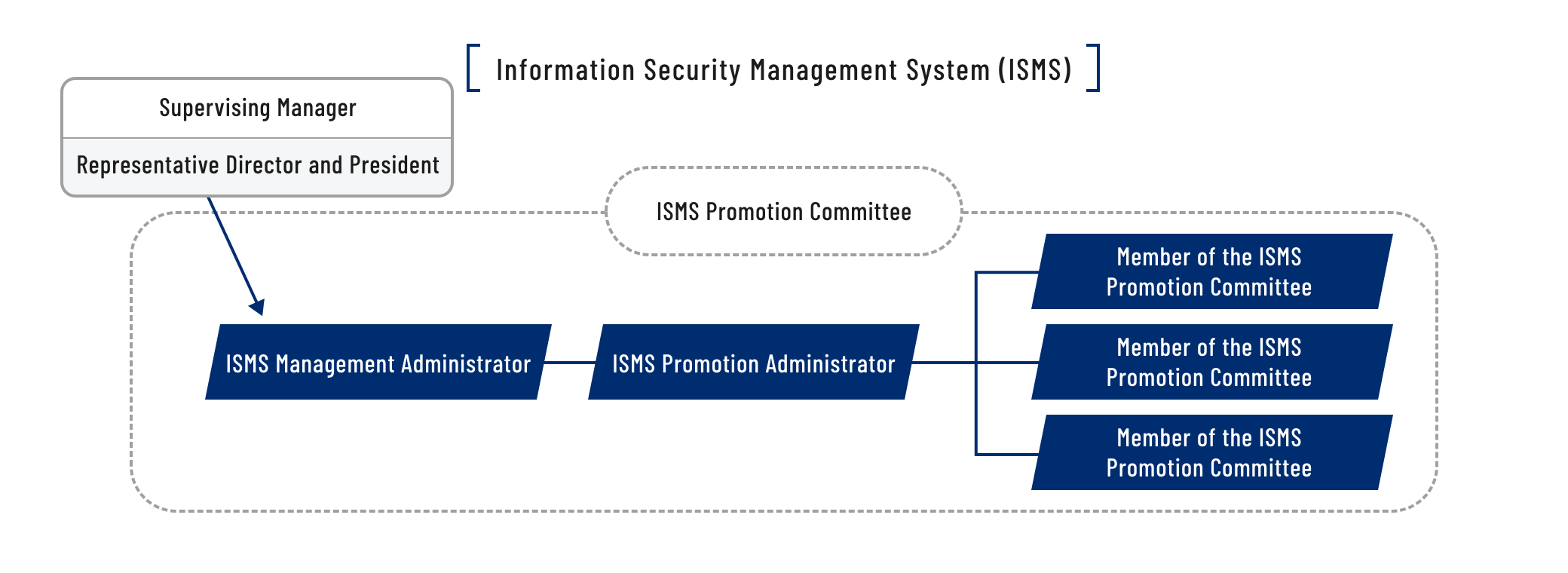
Information Security Policies
All SunFlare Group executives and employees abide by the company's in-house rules concerning information security. We retain our clients' trust by protecting their information assets from threats through the conducting of periodic reviews to ensure safety, confidentiality and availability.
ISO 27001 certification
Keenly aware of the importance of information from past client projects, SunFlare acquired ISO 27001 certification, which is an international standard related to information security management, in December 2013. We have established a system that comprehensively manages all facets of security—including in terms of people, information communication systems, working areas, and supplier management—and conducts periodic reviews to ensure safety.
Information security system and initiatives
- To conform with ISO 27001 specifications, we have established ISMS rules and regulations, including an information security manual. We continuously implement improvement measures based on the conducting of management reviews and periodic internal audits within a security management system.
- We have also established an accountability system and procedures to ensure that we respond quickly, effectively and systematically in the event of an information security incident.
Physical and environmental security measures
- We have installed a system for controlling access to the office area. Employees are allowed to enter the office only after their identity has been authenticated using their IC employee identity card.
- Anyone wishing to visit the office must fill out an admission request form and then wear a visitor card. Visitors are accompanied by an employee at all times while they are in the office area.
Handling and safeguarding of confidential information
- 1. Confidentiality agreements for translators
-
All of our part-time staff, full-time employees and outsourced staff, including translators, enter into non-disclosure agreements and are required to comply with our confidential information management regulations.
- 2. Handling of confidential information
-
- All of the information that we receive from the client is treated as strictly confidential.
- The management requirements stipulated in our confidential information management regulations describe the handling of electronic and paper-based data in terms of the following categories: 1) the copying of confidential information; 2) the disclosure and distribution of confidential information; 3) the electronic transmission and accessing of confidential information; 4) the forwarding of confidential information; 5) the carrying of confidential information; 6) the storage of confidential information; 7) the disposal of confidential information; and 8) the recording of confidential information.
- In accordance with these regulations, translators are required to adhere to restrictions on the printing and copying of the files that they are assigned, to delete the files after the completion of their work, and to submit a report on the status of these files.
- 3. Security training
-
- Employees receive security training when they join the company and on an annual basis thereafter.
- Translators are subject to annual reviews based on our contractor assessment standards.
Implementation and operation of security measures for information systems and communications
- We authorize access to shared information areas on a need-to basis in order to prevent unauthorized access.
- We install and regularly update antivirus software on all of our computers and servers.
- We conduct automatic cloud backups of our server data.
- We conduct system monitoring and log archiving for the main company servers and network devices.
- We operate real-time information sharing for all team members through mailing lists and portal websites with access limited to only those involved in the project.
- We use fiebie, a secure file transfer application, to exchange data with our clients. The backend of fiebie is based on SharePoint Online from Microsoft, allowing for robust security. We use our FilePort system to encrypt all communication pathways when exchanging files with our outsourced staff.
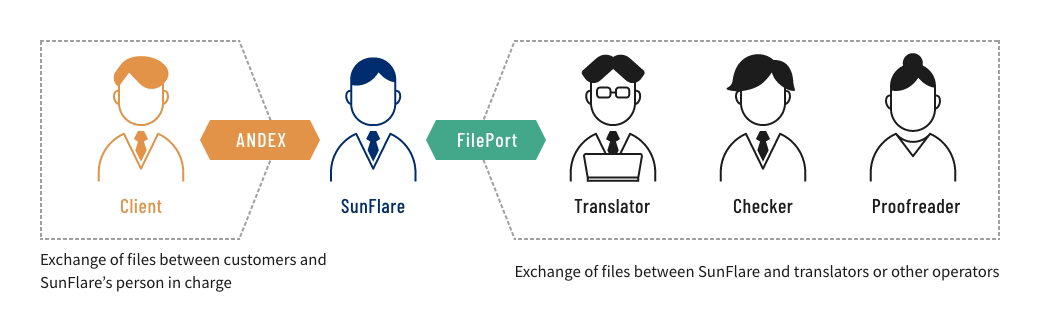
- What is fiebie?
-
The fiebie service is an SaaS used in connection with Microsoft 365.
It provides the function of transmitting and gathering files simply by linking with Microsoft Outlook and entering email addresses for sharing data. - What is FilePort?
-
FilePort is a system that we use to exchange files with translators and other parties working on a project.
All of the files are encrypted so that they cannot be viewed on external systems, thereby enabling data to be transmitted quickly and securely.
Employing these high-security information systems allows us to perform our operations quickly and securely.
Business continuity planning
- We incorporate uninterrupted information security into our business continuity planning (BCP).
- We hold emergency drills once every year.
- We conduct redundancy preparations for stand-by equipment and alternate routing to ensure that we are prepared for any eventuality.
Security system construction
SunFlare's affiliated company ANDROMETEC Co., Ltd. develops and operates our information system infrastructure based on ISMS and PMS.
ANDROMETEC supports our business operations by managing the operation and maintenance of our information security systems during external evaluations and internal audits.
ANDROMETEC Co., Ltd.
Shinjuku Hirose Bldg., 4-7 Yotsuya, Shinjuku-ku, Tokyo, 160-0004, Japan
Privacy mark acquisition
SunFlare handles a wide variety of personal information from clients, employees, SunFlare Academy students, registered translators and content creators, and respondents to recruitment ads.
To ensure that we handle such information appropriately, we acquired a Privacy Mark, which calls for the implementation of stricter management practices than those required under Japan's Personal Information Protection Act, on December 12, 2014. We have also established a personal information protection management system (PMS), for which we conduct employee training sessions to raise awareness of the system's operational rules throughout the company.




